Security services provider BitDefender published information about a DLL sideloading vulnerability of OneDrive that is exploited in the wild. According to the information, malicious actors exploit the vulnerability to mine cryptocurrency on successfully exploited machines.
DLL hijacking is a common occurrence on Windows. Windows uses a priority system to determine from which location a DLL file is loaded, when a full path is not specified by an application. DLL hijacking attacks abuse that system to plant malicious files at a location with a higher priority. The program will then load the malicious DLL instead of the legitimate DLL file.
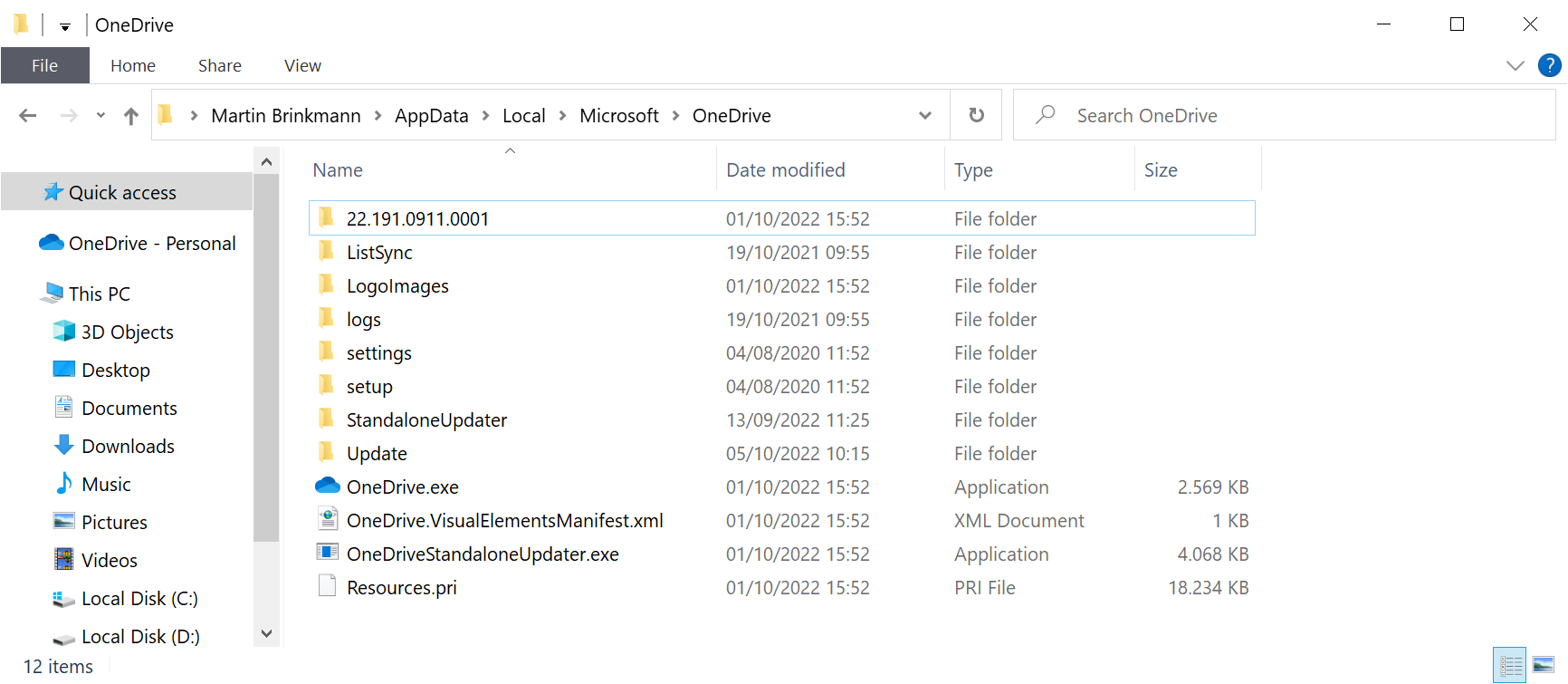
In the case of the OneDrive malicious campaign, the attackers make use of that concept to plant a malicious DLL file into the user folder on the system. Specifically, a fake secure32.dll DLL file is written to %LocalAppData%\Microsoft\OneDrive\ in a non-elevated process. This malicious dynamic link library is then loaded by the two OneDrive processes OneDrive.exe and OneDriveStandaloneUpdater.exe.
The OneDrive updater process is scheduled to run once per day already, which ensures that the malware is loaded at least once per day on the system, provided that it is not detected by antivirus software. The malicious actors are adding OneDrive.exe to the startup of the operating system as well to “make persistence even more robust”.
When the fake DLL is loaded for the first time, it downloads cryptocurrency mining software to the infected PC system to run it.
“Once loaded into one of the OneDrive processes, the fake secur32.dll downloads open-source cryptocurrency mining software and injects it into legitimate Windows processes.”
BitDefender notes that while the attack is limited to cryptocurrency mining currently, the attackers have options to switch to other malicious attacks, including ransomware or spyware deployments.
The security company recommends that OneDrive is installed “per machine” instead of “per user” on Windows machines to avoid the DLL hijacking vulnerability. Attackers do need to penetrate Windows PCs successfully in the first place to save the malicious DLL file in the OneDrive user directory. A reliable protection against malicious threats as well as the use of common sense should prevent the attack in the first place.
Windows users and administrators may check the OneDrive installation on Windows PCs to find out if the malicious DLL file has been planted on the system already. To do so, load %LocalAppData%\Microsoft\OneDrive\ in File Explorer and search for the file in the OneDrive directory.
Thank you for being a Ghacks reader. The post OneDrive DLL Sideloading vulnerability exploited in the wild appeared first on gHacks Technology News.
